Hard-drive security flawed in millions of computers
-
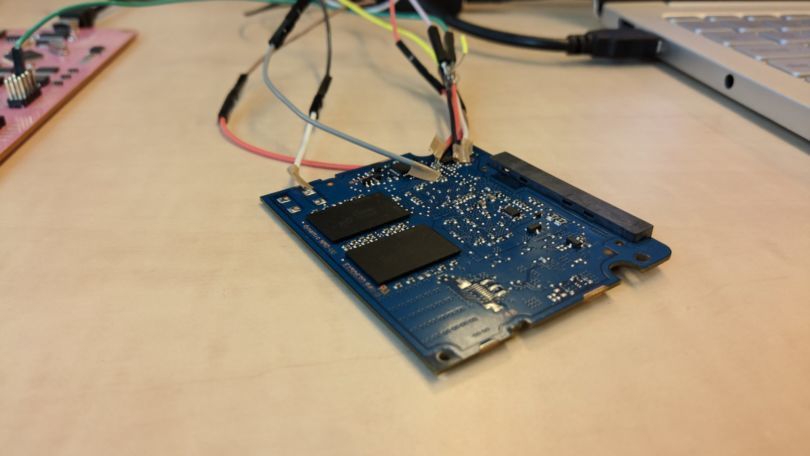 Manipulating the software. Photo: Carlo Meijer
Manipulating the software. Photo: Carlo Meijer
It has turned out that certified “secure” data storage devices in millions of computers across the globe do not seem to deserve that designation. Digital security researchers from Nijmegen discovered that the built-in encryption of the hard disks can be bypassed. Manufacturers Samsung and Crucial were notified six months ago, and are announcing it publicly this week.
High-level managers from Samsung came from South Korea to the Netherlands in the spring to hear what the researchers from Nijmegen had discovered. Could the encryption of their hard drives be bypassed? The answer is yes, according to Bernard van Gastel and Carlo Meijer. By manipulating the disks, they could access the data without a password, whereas that should expressly not be possible. It pertains to hard disks used in ordinary computers around the world.

Soldering
Hardware encryption is specifically important for hospitals, ministries, and organisations such as the police. Without a password, no one should be able to access sensitive information.
‘Manufacturers like Samsung and Crucial supply SSDs with built-in encryption, the user only needs to set their own password,’ says Van Gastel. ‘That encryption is air tight, or so they say. But that is not true.’
That is what PhD candidate Meijer discovered after cycling home with Van Gastel one day. They had been chatting about how these disks are put together, and where weaknesses could exist. Meijer started tinkering at home.
‘You solder on a few wires and try to manipulate the software.’
A chip on the circuit board contains the software. You solder a few wires onto it, and try to manipulate the software so it skips the password check. To my surprise, it worked. I got to the data without a password.’ Excited, he immediately rang his colleague.
Information given to organisations
That is how the research started. Meijer and Van Gastel managed to bypass the encryption on different models of solid-state and portable drives that are for sale in shops. The results were so alarming that they contacted the National Cyber Security Center (NCSC). Van Gastel: ‘As researchers, we had the task to break this news responsibly. The manufacturers were informed and were given six months to resolve the issue.

Confidentially, large organisations worldwide – including Radboud University – were informed with the recommendation to check their computers for the hardware used and to install additional security measures where necessary. There is a chance, of course, that computer fanatics will also try to bypass the encryption after this news is revealed. ‘We suggest using additional software,’ says Van Gestel. ‘Like VeraCrypt. It is free to download, and so far, research has found no vulnerabilities.’
Risks
The security risk may also apply to personal computers, but the consequences are unlikely to have the same impact when an ordinary citizen leaves their laptop on the train and a malicious person then starts soldering it. Meijer: ‘But if, for example, it is a laptop owned by someone who works with the Ministry of Justice, a data leak can be very dangerous. And it is more likely that you treat your computer more casually if you are convinced that it is encrypted properly.’
Today, the researchers will break their news to the rest of the world, and a scientific publication will follow. They don’t yet know what the manufacturers have done with their warning. ‘We will wait and see what they have come up with.’
What data storage devices are impacted?
Crucial and Samsung combined supply about half of all SSD storage drives. Their main models (at the time the issues were discovered) were found to be vulnerable. Whether problems will occur depends on if and in what way the encryption on the disk is activated. Windows encryption, named BitLocker, is automatically disabled when it detects built-in hardware encryption, and is therefore also compromised. The models are:
- Crucial (Micron) MX100, MX200, and MX300 internal hard drives
- Samsung T3 and T5 portable USB hard drives
- Samsung 840 EVO and 850 EVO internal hard drives



